Recently, I was helping my eCommerce client who has hired me multiple times to help improve their SQL Server Performance. During the recent Comprehensive Database Performance Health Check, I realized that their DBAs are logging into their server with a blank or empty password. This is a very dangerous and extremely Bad Practice. Let us discuss it today.

Bad Practice – Empty Password
While working together on SQL Server Performance Health Check, there was a situation where we had to log in to SQL Server. If you have read my earlier consulting blog post, you would know that I never ask for the username and password of the server from my client. However, during the screen share, I noticed that DBAs were just logging into the system with the empty password and SA username.
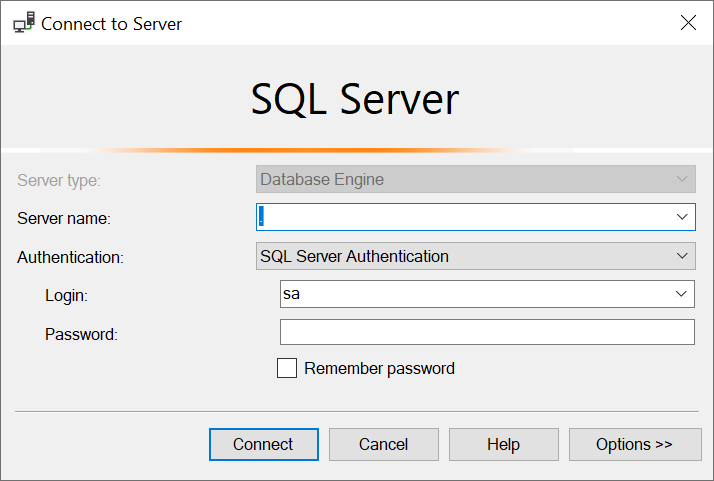
I had to immediately stop my consultation at the point. I have a strong personal policy to not continue the consultation if I come to know any security details of clients with or without their knowledge. I informed the DBA on the call that I will be not able to continue till they have a valid (and not known to me) password for their production system.
After further investigation, we discovered that their lead DBA had accidentally run the following code on their server, which had removed the password from their SA and now everyone was using it.
USE [master] GO ALTER LOGIN [sa] WITH PASSWORD=N'' GO
It is really very bad practice to keep the SA password to empty as this username can do pretty much everything on the server. Many organizations keep the SA username itself disabled so intruders can’t get inside it. If you have to keep sa username enabled, it is recommended that you keep a very complex password for the same.
Here are a few blog posts related to the topic:
- SQL SERVER – DISABLE and ENABLE user SA
- Can Admin Rename SA Account in SQL Server? – Interview Question of the Week #256
- How to Change Owner of Database in SQL SERVER? – Interview Question of the Week #117
Reference: Pinal Dave (https://blog.sqlauthority.com)





